Login authenticators control how users log in to CXone Mpower. CXone Mpower supports both internal and external authentication based on the login authenticator that is assigned to the user and the type and configuration of that login authenticator. There are two types of login authenticators:
-
System authenticators, which use the CXone Mpower system itself to authenticate users with a username and a password.
-
External authenticators, which use federation to authenticate users with an external identity provider (IdP).
You can read more about authentication and authorization in CXone Mpower.
Login Authenticators and User Password Changes
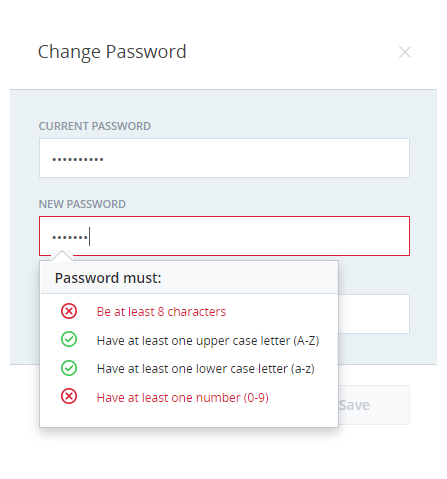
You can create your own login authenticators for different roles in your organization. After you configure a login authenticator for a particular role, the password field displays the configured login authenticator rules when a user tries to set or change the password.
As the user types in the password, CXone Mpower displays the login authenticator rules. CXone Mpower evaluates the password based on the login authenticator rules and color codes the rules in real time. Rules that the password meets appear in green and are marked with a checkmark. Rules that are not met appear in red and are marked with X.
Key Facts About Login Authenticators
- When the login authenticator (LA) is modified, changes become effective as soon as they are saved. Users who are logged in at the time of the change are not affected but are redirected to change their password upon their next login if their password does not meet the requirements of the new LA.
- You can assign login authenticators directly to users. Users can only be assigned to one LA. Users don't have to be assigned to a login authenticator, but they won't be able to log in to CXone Mpower without one. Backend users and integrations can log in with their assigned access keys without having to be assigned to an LA.
- You can select a required location for the login authenticator as a set of IP addresses, ranges or subnets. If you do this, users without both the correct credentials and location cannot log in.
- With OpenID Connect login authenticators, you can set up single logout with your IdP. To do so, you have to include an End Session Endpoint in the LA. You also have to whitelist the Signout Redirect URI in your IdP.
-
For system login authenticators:
-
You can specify the number of days the password is valid. After the specified number of days, the users in the relevant role are prompted to change their passwords.
-
You can specify the number of previous passwords that CXone Mpower remembers. Users cannot reuse passwords that CXone Mpower remembers.
-
If a user enters the wrong password six times, the account is locked for 30 minutes. As an administrator, however, you can unlock a user's account sooner than 30 minutes.
-
If a user forgets the password, the user can request a password reset link be sent by email.
-