This page guides you, step-by-step, in setting up authentication for your CXone Mpower system using SecureAuth as your external identity provider (IdP).
Before You Begin
- Gain a basic understanding of authentication and authorization concepts and terminology if you've never set up a process like this before.
- Review the CXone Mpower-specific process if this is the first time you've worked with authentication in CXone Mpower.
- Consider your human users and the levels of access they need. Decide whether people with greater access should have greater levels of security.
- Decide whether you will use custom password requirements, multi-factor authentication (MFA), or both.
- Based on your decisions, make a list of login authenticators. The list should include the password requirements and MFA status you want to use for each login authenticator.
- Consider whether you need to include authentication and authorization for applications like bots or intelligent virtual assistants (IVAs). If so, you will need to create access keys.
- Gain an understanding of the SAML 2.0 authentication protocol. CXone Mpower supports SAML 2.0 for SecureAuth integration.
- Evaluate the combination of IdP and protocol to ensure your use cases and user flows are supported, and to identify potential issues. This should include actual testing.
- Implementing changes to authentication and authorization whenever a need comes up will likely cause issues in your system. You can avoid these problems by creating an implementation plan. Your CXone Mpower team can support and guide you in this planning process. Good planning makes for a smoother implementation.
Create and Configure the SecureAuth Application
-
Log in to your SecureAuth management account.
-
On the left side of the Identity Platform page, click Application Manager.
-
Click Add an Application.
-
From the list of application templates, select SAML Application.
-
On the Application Details page, set the following configurations:
-
Enter an Application Name. For example, you could enter CXone Mpower.
-
Select the Authentication Policy for this application.
-
Enter the Data Stores to authenticate and allow user access for this application.
-
Select any necessary Groups to allow access to this application.
-
-
Click Continue.
-
In the Configure Connection section, set the Connection Type to SP-initiated and select By Post.
-
In the User ID Mapping section, set the User ID Profile field and Name ID Format to your preference. The User ID Profile field will determine the value that you will enter in the External Identity field of the CXone Mpower user's profile.
-
In the SAML Assertion section, set the following configurations:
-
In the Assertion Consumer Service (ACS) field, enter https://cxone.niceincontact.com/need_to_change. You will change this value to the ACS URL you receive later from the CXone Mpower Login Authenticator.
-
In the Audience field, enter https://cxone.niceincontact.com/need_to_change. You will change this value to the Entity ID you receive later from the CXone Mpower Login Authenticator.
-
In the IdP Signing Certificate field, click Select Certificate, choose the IdP signing certificate to use, then click Select to close the box.
-
In the Signing Algorithm field, select SHA1 or SHA2. CXone Mpower supports both options.
-
In the Sign SAML Assertion field, disable signing the SAML Assertion. CXone Mpower doesn't support this.
-
In the Sign SAML Message field, enable signing the SAML Message.
-
In the Encrypt SAML Assertion field, disable encryption of the SAML Assertion. CXone Mpower doesn't support this.
-
-
Click Add Application.
-
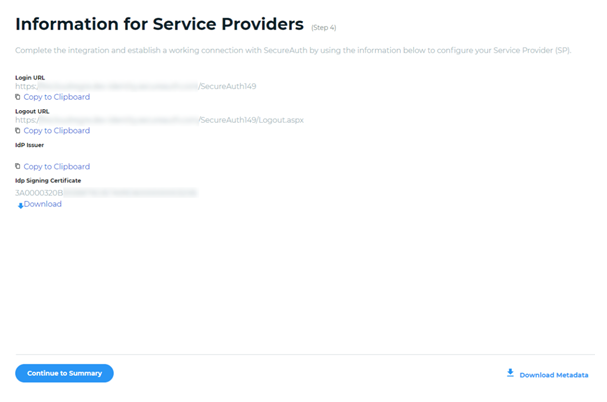
From the Information for Service Providers page:
-
Copy the Login URL. This will be used for the Endpoint URL in the CXone Mpower Login Authenticator.
-
Download the IdP Signing Certificate. This will be uploaded to the CXone Mpower Login Authenticator.
-
-
Click Continue to Summary.
-
Click Back to Application Manager to find the application now added to the list.
Setup an External Login Authenticator in CXone Mpower
- In CXone Mpower, click the app selector
 and select Admin.
and select Admin. - Click Security > Login Authenticator.
- Click New Login Authenticator.
- Enter the Name and Description of the Login Authenticator.
- Select SAML2 as the Authentication Type.
-
If you want to require that users log in from a certain IP address, select the Location you set up in the preceding section.
- Paste the Login URL obtained previously from SecureAuth into the Endpoint URL field of the Login Authenticator.
- Click Choose File and select the certificate saved previously from SecureAuth.
- Click Save and Activate.
- Open the Login Authenticator you just created.
- Copy both the Entity ID and ACS URL, as you will need them in the next task.
Complete the SecureAuth Configuration
-
Log in to your SecureAuth management account.
-
On the left side of the Identity Platform page, click Application Manager.
-
Select the new application that you created.
-
Edit the Connection Settings:
-
In the Assertion Consumer Service (ACS) field, enter the ACS URL you copied from the CXone Mpower Login Authenticator.
-
In the Audience field, enter the Entity ID you copied from the CXone Mpower Login Authenticator.
-
Assign the Login Authenticator and Configure User Federated Identity
- In CXone Mpower, click the app selector
 and select Admin.
and select Admin. - Click Users, and search for an employee that will be signing in using SSO.
- Click Edit.
- Select the General tab.
- In the Security section, select the Login Authenticator you previously created from the Login Authenticator drop-down.
- In the Federated Identity field, enter the user's unique NameID from SecureAuth.
- Click Done.
Verify User Access with SecureAuth Single Sign-On
-
Have one or more test users log in by opening a browser and navigating to https://cxone.niceincontact.com. FedRAMP users will navigate to https://cxone-gov.niceincontact.com.
-
When you're ready, roll out your IdP Single Sign-on configuration to all CXone Mpower users.
For additional SecureAuth configuration information, refer to SAML application integration![]() .
.